How To
How to use Tor to browse the web like a pro

- August 9, 2022
- Updated: July 2, 2025 at 3:32 AM

The dark web has developed a reputation as a frightening space to carry out serious criminal activity. While that’s a fair assessment, this subsection of the deep web also provides a way for activists and journalists in autocratic nations to share information anonymously. To safely access the deepest subsegments of the internet, you’ll need a special browser such as Tor. And while Tor is a great solution for online privacy, understanding how to use it in a way that protects your sensitive information is critical.
As an online privacy tool, Tor is entirely legitimate, with plenty of upsides, but using the Tor browser does carry risks. The dark web remains a haven for cybercriminal behavior and malware. Following the wrong link can expose your personal data and potentially result in a significant IT disaster. The best approach to securely browsing Tor is to connect to a virtual private network (VPN). This article discusses how the Tor browser works and how you can safely leverage it to stay anonymous online.
What are the surface web, deep web, and dark web?
The surface web, aka the regular World Wide Web that we use every day, makes up only about .03% of the internet. This includes all the websites, social media, e-commerce pages, blogs, and anything else indexed by Google. The rest of the internet falls within the deep web, which is anything not indexed by web crawlers. These sites include everything from your personal email and payment portals to private forums and hidden backend web pages. The dark web is a small segment of websites on the deep web with hidden IP addresses that can only be accessed by special browsers like Tor. While the surface and deep web contain mostly benign sites, dark web sites use encryption software to keep their users and locations concealed.
What is Tor?
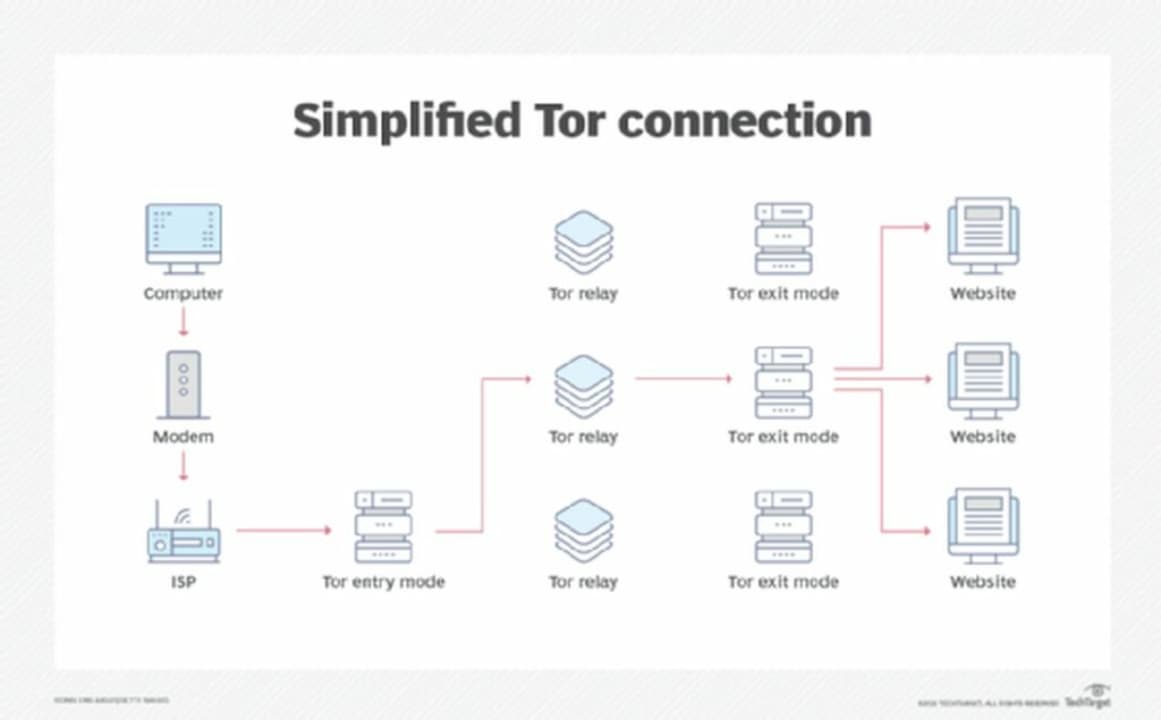
Short for The Onion Router, Tor is a free, open-source software that lets you browse the internet anonymously. The Tor browser relies on encryption layers to anonymize your traffic through a random relay. This process repeats itself three times across a decentralized network of nodes or a circuit, maintained and operated by volunteers and online privacy advocates. In short, this browsing method makes your information difficult to track. And, generally speaking, Tor prevents sites from determining the location of your IP address.
As your encrypted traffic passes through these randomized nodes, Tor eliminates your browsing history by removing cookies after each browsing session. Likewise, Tor deploys several other mechanisms to block and reduce your exposure to trackers. The browser identifies surveillance trackers that follow web users across different sites and introduces an additional circuit that tricks surveillance trackers into interpreting the connections as two distinct users. This means that questionable websites can’t trace your activity or identify you when you log in to another site.
Downloading and using Tor
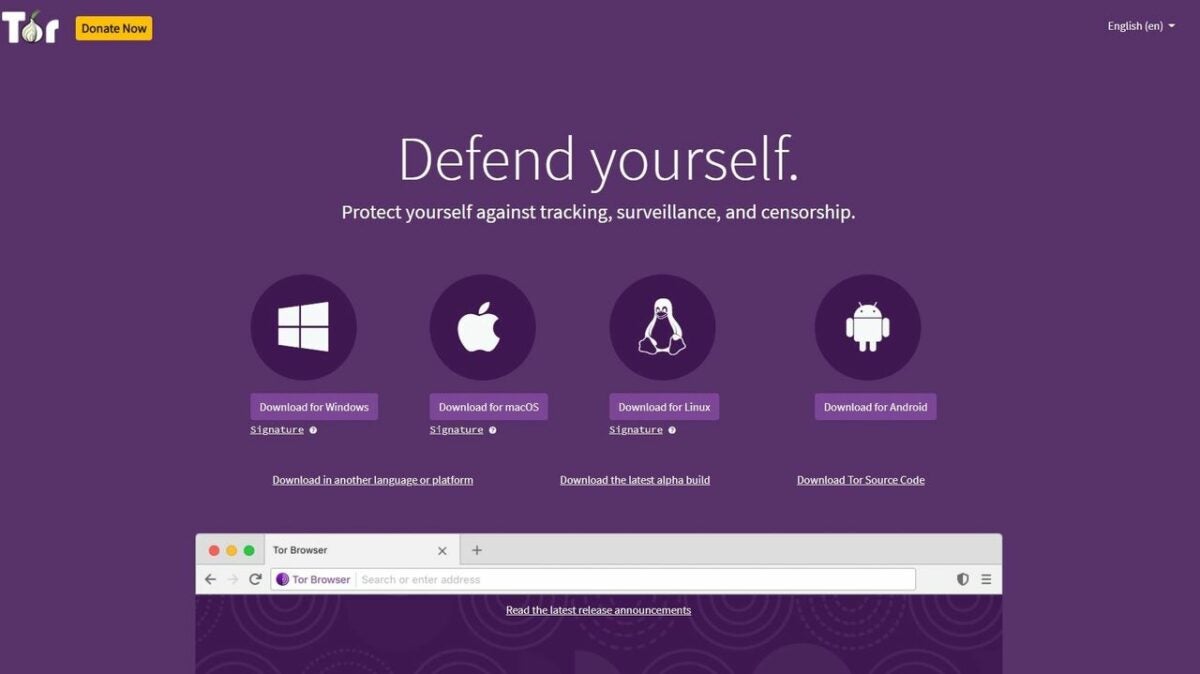
Downloading Tor is simple and fast, and you can access the software at your preferred application discovery site. Versions for your desktop PC and Android devices are available. You’ll also find an unsupported onion browsing edition for iOS. It is worth noting that Tor is blocked in several countries, and you may not be able to use it on specific networks, such as those controlled by corporations and universities where Tor is often banned for security reasons.
Upon initiating a Tor session, the browser presents the option to Connect or Configure. If you must access the Tor browser where the network is prohibited, you need to choose Configure. This option allows you to circumvent the blocked access through an array of custom browser configurations. Configuring the browser lets you occlude your traffic through pluggable transports that randomize Tor traffic and, instead of connecting to the onion network, make it appear as if your traffic is diverting to major sites such as Amazon. In the event that you cannot access the Tor browser, you can try one of the recommended configurations to bypass any blocks on the network.
As previously discussed, security is a big issue with Tor. The browser offers various security settings that you can review by selecting the onion icon at the top left of your screen. Click on Security settings to display an intensity slider that allows you to adjust your security settings from standard to safest. The medium safer setting disables JavaScript on HTTP sites and prevents you from using some fonts, while audio and video will never play automatically. In other words, you have to manually press play to run audio and video in safer mode. The safest security setting disables JavaScript completely.
Accessing the dark web with Tor
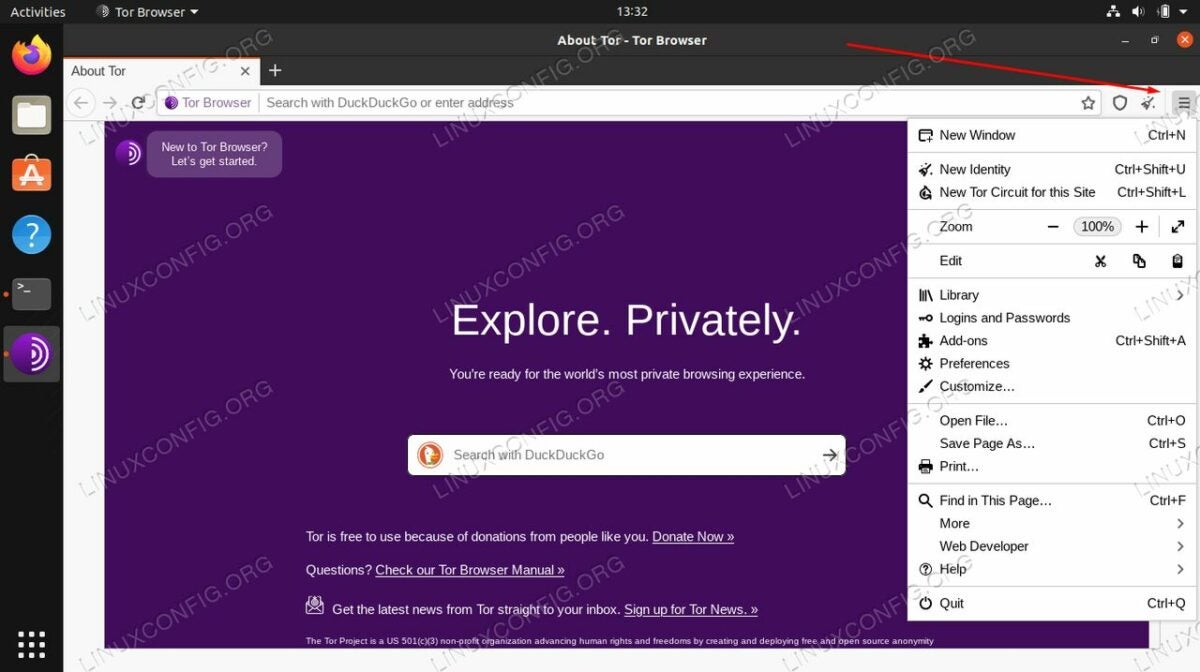
Tor works like any other browser, but launching it is slightly more involved. In theory, you could do all your browsing in Tor, but it is far too slow to do this with any reasonable efficiency. You are more likely to encounter more CAPTCHAs than usual because the browsing behavior is considerably different from your other conventional options.
The use of VPNs when browsing the dark web with Tor can’t be stressed enough. However, the downside to virtual private networks is that they create security bottlenecks. All your traffic must necessarily run through the VPN. This means you have to trust the provider to act as a new ISP, whereas Tor is an inherently private decentralized network.
Tor and your online privacy
While Tor is an effective tool for browsing anonymously online, it is far from perfect. Even though pinging via Tor nodes is a challenge, it’s still possible. Furthermore, the dark web remains a haven for criminal hackers, spies, and other bad actors. Tor may not be a foolproof solution, but it is the best choice as of now for safeguarding your sensitive information online while navigating the dark web. Interested in improving your network security? Consider downloading these free antivirus and VPN software solutions.
You may also like
 News
NewsMillions of PS4 users will not be able to play this RPG starting next year
Read more
 News
NewsStranger Things is getting ready for its grand finale and its creators have already revealed some sneak peeks
Read more
 News
NewsMatt Smith, the iconic Doctor Who, will be a villain in the upcoming Star Wars movie
Read more
 News
NewsThe K-Pop warriors continue to dominate and could become the most-watched movie in Netflix history
Read more
 News
NewsThe cybersecurity landscape is preparing for an increase in AI-driven attacks
Read more
 News
NewsGeneration Z wants to laugh, and this is how the content they consume shows it
Read more
